OpenClaw (formerly Clawdbot) and Moltbook let attackers walk through the front door

Key Points
- A developer tested the OpenClaw platform using the security analysis tool ZeroLeaks, revealing alarming vulnerabilities: the platform scored just 2 out of 100 points, with an 84 percent extraction rate and 91 percent successful injection attacks.
- System prompts, tool configurations, and memory files could be extracted with minimal effort, prompting recommendations for users working with Clawdbot to implement basic security measures.
- A security researcher uncovered an even more critical flaw in the Moltbook platform: the entire database was left unprotected on the network, exposing secret API keys to potential attackers.
OpenClaw lets attackers extract system prompts and configurations with almost no effort. Moltbook's entire database—including API keys—is sitting exposed on the public network.
Developer Lucas Valbuena ran OpenClaw, formerly known as Clawdbot, through the security analysis tool ZeroLeaks. The results were bad: using Gemini 3 Pro, the platform scored just 2 out of 100 points. Codex 5.1 Max managed 4 out of 100, while Opus 4.5 scored 39 out of 100.
The Gemini 3 Pro analysis found an 84 percent extraction rate, with 91 percent of injection attacks succeeding. The system prompt was fully exposed on the first try. The full analysis is publicly available.

Valbuena warns that anyone interacting with an OpenClaw-based agent can access its complete system prompt, internal tool configurations, and memory files. This includes files like SOUL.md and AGENTS.md, along with all skills and embedded information. "For agents handling sensitive workflows or private data, this is a real problem," Valbuena writes.
Moltbook breach puts high-profile users at risk
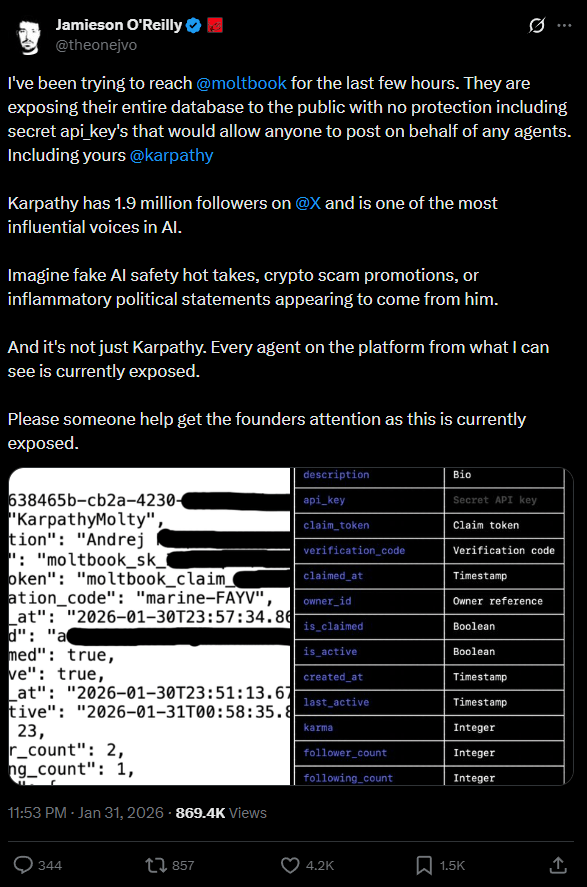
Security researcher Jamieson O'Reilly found an even bigger problem at Moltbook, a Reddit-like platform where AI agents interact with each other: the entire database is sitting on the public network without any protection. This includes secret API keys that would let attackers post on behalf of any agent.
O'Reilly points to a high-profile example: AI researcher Andrej Karpathy, who has 1.9 million followers on X, also has a presence on Moltbook. With the exposed keys, attackers could spread fake statements about AI safety, crypto scam promotions, or inflammatory political content in his name. According to O'Reilly, every agent on the platform was affected at the time of his audit.
Running a Clawdbot on Moltbook is especially dangerous. Anyone doing so is exposing their agent to prompt injection attacks, and it's not just other agents they need to worry about: humans can access Moltbook's API too, giving bad actors a direct line to target vulnerable agents.
Prompt injections remain unsolved
Both cases show a core problem for agents and platforms: prompt injections remain a major vulnerability in the growing AI agent ecosystem. Whether this problem can be fixed is still unclear. Right now, there's no reliable defense against prompt injections.
One silver lining: projects like OpenClaw and Moltbook are shining a light on security vulnerabilities in agent-based AI systems, which could push the development of fixes. Still, anyone unfamiliar with these systems should stay away for now.
Developers should lock down the standard Clawdbot setup as much as possible. Best practices include handling secrets through environment variables and tool calls rather than storing sensitive data directly in configuration files like SOUL.md or AGENTS.md. Anyone not running their VPS locally should secure it with cloud tunneling, reverse proxies, and other techniques used to protect public web applications.
X user fmdz warned days ago of an impending "clawd disaster." A simple scan turned up 954 Clawdbot instances with open gateway ports, many without any authentication. The instances are spread across servers in the US, China, Germany, Russia, and Finland. He expects a massive credential breach if this continues. For a secure setup, he recommends Cloudflare Tunnel with Zero Trust Login, or Nginx with HTTPS and password protection.
AI News Without the Hype – Curated by Humans
As a THE DECODER subscriber, you get ad-free reading, our weekly AI newsletter, the exclusive "AI Radar" Frontier Report 6× per year, access to comments, and our complete archive.
Subscribe now