OpenAI's Operator Agent gets o3 upgrade for more precise browser control

OpenAI's computer-using agent is getting an upgrade: The new o3 model is designed to make Operator more precise, more structured and more successful on the web.
OpenAI has equipped its Operator agent in ChatGPT with a new model based on the o3 architecture. The new model replaces the previous GPT-4o-based version of Operator and is available worldwide in ChatGPT-Pro as a research preview. API usage is still based on GPT-4o.
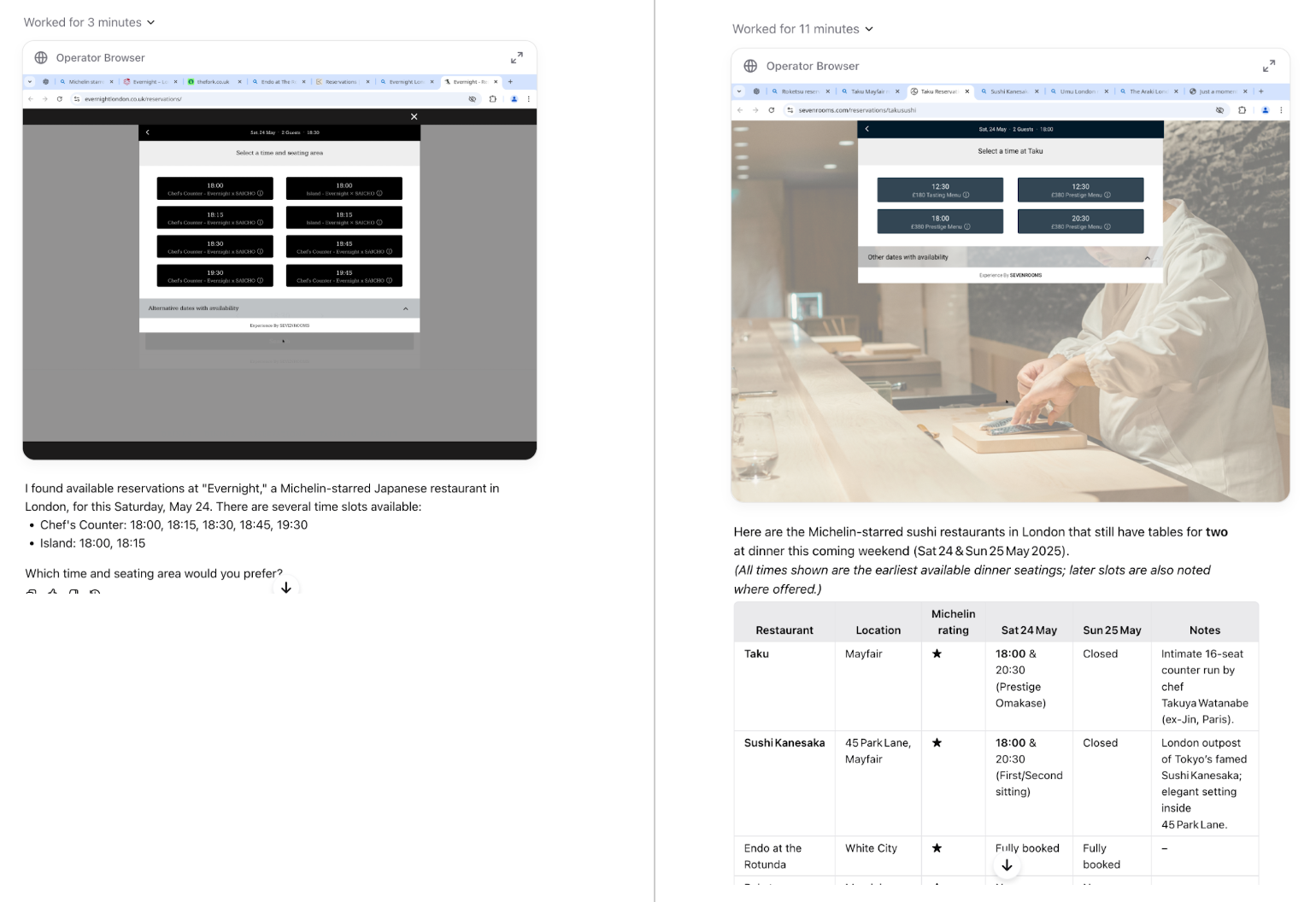
Operator, which OpenAI calls a Computer-Using Agent (CUA), can navigate websites just like a person - scrolling, clicking, and typing text to automate complex tasks. OpenAI first introduced Operator as a research preview in January 2025, aiming to create an AI agent that performs web-based actions the way humans do, potentially automating many knowledge-worker tasks.
More structure, higher success rate
With the switch to o3, Operator is designed to be noticeably more robust and effective at completing tasks on the web. OpenAI says the new model interacts more precisely with browsers and produces answers that are better structured and more comprehensive. Internal testing shows Operator now succeeds more often at handling complex workflows.
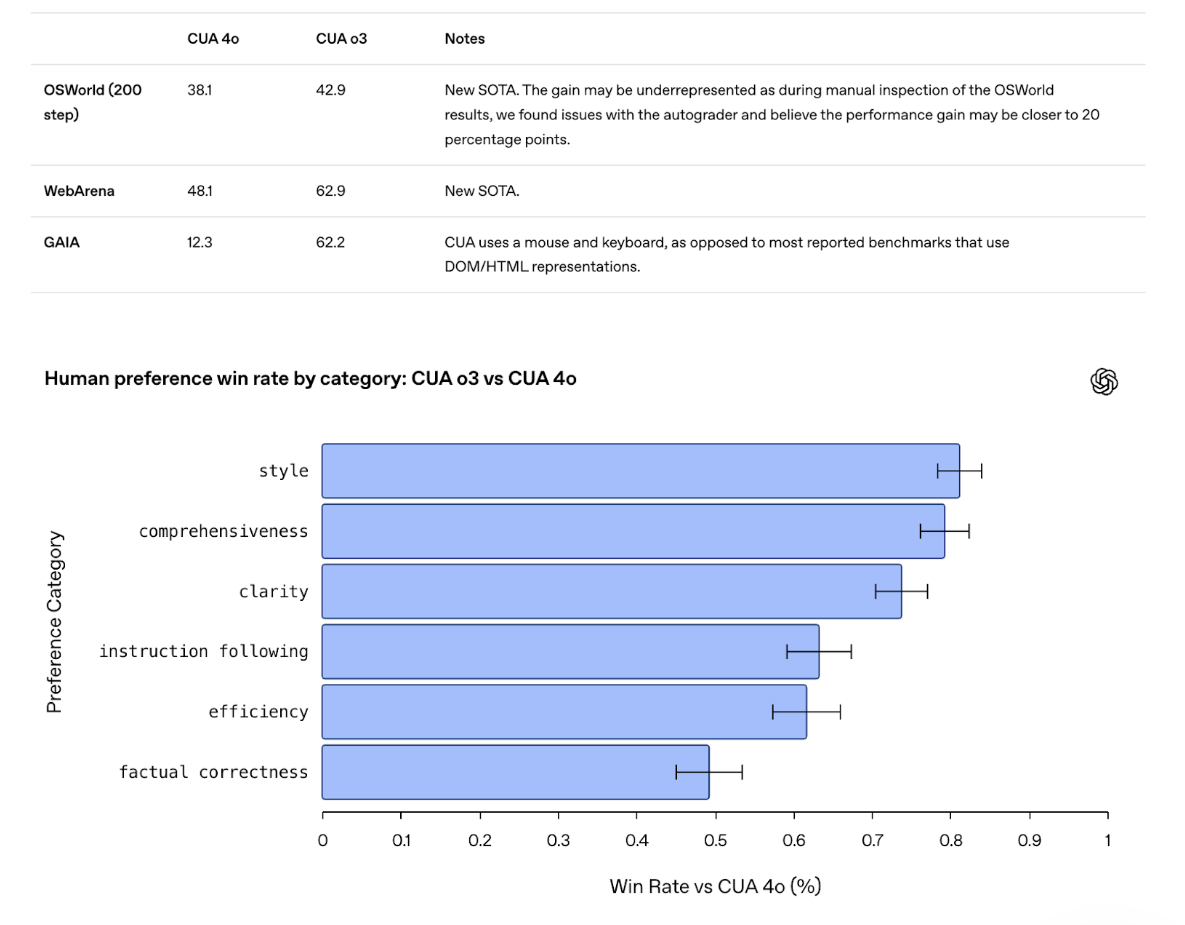
OpenAI says the new model sets the standard in benchmarks like OSWorld and WebArena. User tests also show it delivers better response quality than its predecessor.
Fine-tuned for safer web automation
The o3 Operator model is built on the same architecture as other o3 models, but it has been specifically trained to operate computer interfaces. OpenAI says the model was fine-tuned with additional security data to help it learn when to provide confirmations or refusals. Despite inheriting o3's coding capabilities, o3 Operator doesn't have direct access to coding environments or terminals, OpenAI notes.
Browser automation comes with its own risks: these agents must analyze website content and interpret it as instructions—essentially, prompts. That means attackers could design malicious sites intended to trick the agent into taking unwanted actions, such as entering sensitive information into fake login forms.
AI News Without the Hype – Curated by Humans
As a THE DECODER subscriber, you get ad-free reading, our weekly AI newsletter, the exclusive "AI Radar" Frontier Report 6× per year, access to comments, and our complete archive.
Subscribe nowAI news without the hype
Curated by humans.
- Over 20 percent launch discount.
- Read without distractions – no Google ads.
- Access to comments and community discussions.
- Weekly AI newsletter.
- 6 times a year: “AI Radar” – deep dives on key AI topics.
- Up to 25 % off on KI Pro online events.
- Access to our full ten-year archive.
- Get the latest AI news from The Decoder.