If unsecured ChatGPT accounts end up on the darknet, it's not OpenAI's fault

At least 100,000 credentials of ChatGPT users were reportedly leaked to the darknet. OpenAI released a statement regarding the incident.
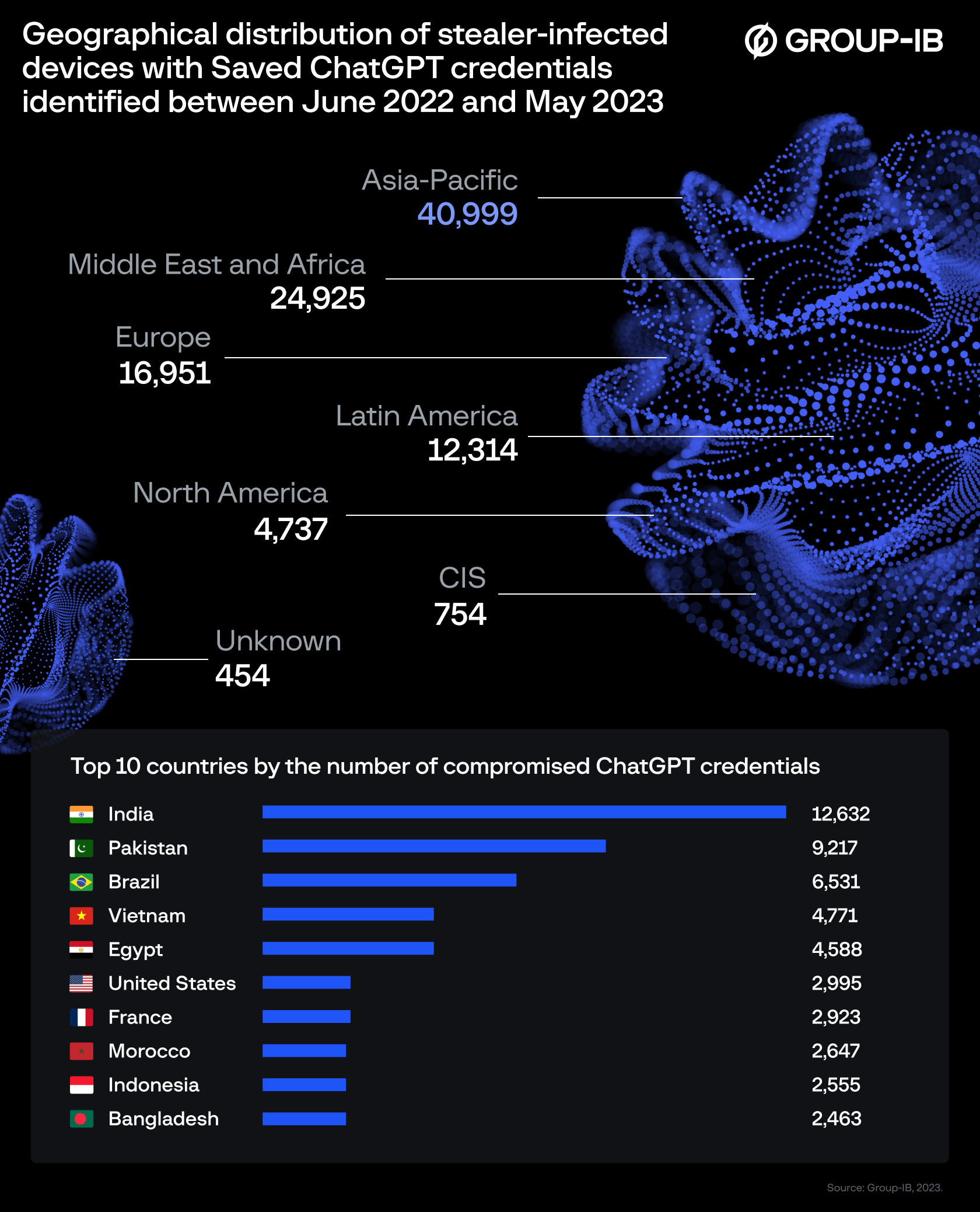
Most of the affected users are from the US, France, Morocco, Indonesia, Pakistan and Brazil. The oldest data is said to date back to June 2022. ChatGPT was made publicly available in November 2022.
Two days after the first reports of the darknet incident, OpenAI issued a statement to Tom's Hardware. The company insists that neither it nor its users were targeted and that the leaked accounts are under investigation.
Getting ChatGPT accounts has never been easier
According to security analysts at Group-IB, most of the compromised credentials were found in logs associated with various malware. Topping the list is the supposedly easy-to-use Raccoon software, which is responsible for 78,348 compromised accounts.
The results of the Group-IB Threat Intelligence Report are "the result of commodity malware on people's devices and not a breach of OpenAI," an OpenAI spokesperson said.
He added that OpenAI follows industry best practices for user authentication and authorization, and encourages users to use strong passwords and to install only vetted and trusted software on their computers.
ChatGPT is a sensitive target
It is not uncommon for sensitive data to fall into the wrong hands in account leaks. In the case of ChatGPT, however, the impact could be particularly dramatic: because ChatGPT stores all chats by default, attackers could inadvertently gain access to a "treasure trove of sensitive information" with the logins. People use ChatGPT to chat about all kinds of topics, including sensitive personal or business information.
Samsung, for example, banned the use of ChatGPT for fear of data breaches after a case came to light in which company employees entered confidential codes. Employees still using ChatGPT at Samsung could be fired. Apple has also banned ChatGPT.
In response to political pressure, OpenAI implemented an opt-out feature in late April that automatically deletes all chats and removes them from training materials. For the more than 100,000 leaked accounts, this comes too late: according to security researchers, the leaked data has long been for sale on the darknet. It can't hurt to change your password.
AI News Without the Hype – Curated by Humans
As a THE DECODER subscriber, you get ad-free reading, our weekly AI newsletter, the exclusive "AI Radar" Frontier Report 6× per year, access to comments, and our complete archive.
Subscribe nowAI news without the hype
Curated by humans.
- Over 20 percent launch discount.
- Read without distractions – no Google ads.
- Access to comments and community discussions.
- Weekly AI newsletter.
- 6 times a year: “AI Radar” – deep dives on key AI topics.
- Up to 25 % off on KI Pro online events.
- Access to our full ten-year archive.
- Get the latest AI news from The Decoder.